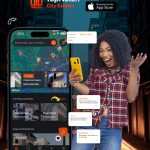
Defaced Site / Took Offline
In some cases hackers replace your content with their own. The most common was political content from terrorist groups and the like. The next most common was hackers simply bragging that they hacked your site. In all of these cases the attacker is doing absolutely nothing to obscure what they have done, anyone who visits the site immediately knows that you’ve been hacked.
In other cases the attackers just destroy your site in some way, taking it offline. Based on what we see when performing forensic research on hacked sites, in the majority of these cases the attacker just screwed up what they were doing and accidentally took your site down.
Example of defaced website courtesy of opennet.net
What’s in it for the attacker?
For the attackers who replace your site with political propaganda, your site is just free advertising for their cause. Those that brag about taking your site down are looking for recognition.
Send Spam
Spam email continues to be a huge issue. According to Statistica, 54.4% of all email traffic on the internet was spam in December of 2015. According to our survey respondents, 19.8% of compromised WordPress sites are used to send email spam.
In many cases the site owner was not aware that it was happening for quite some time. In some cases they notice a slow down in site performance or a spike in server utilization that tips them off. Or their host recognizes it and alerts them.
Unfortunately a very high percentage don’t find out until their domain has been blacklisted by spam watchdog services like Spamhaus. If you depend on email for communication with your customers or others it can have devastating consequences.
What’s in it for the attacker?
The attacker gets two huge benefits. First they get to use the server resources that you’re paying for free of charge. Second, until they ruin your reputation, their email delivery benefits tremendously from originating from your domain and IP address. Ultimately they are trying to get people to click through to their malicious websites.
SEO Spam
There are a number of ways attackers can leverage your website to improve their search engine rankings. The first is to simply host pages on your domain, accruing the benefits of your Domain Authority and clean reputation. Example page below.
The next is to plant links throughout your site to the site(s) they want to give an SEO boost. Since backlinks are still the most important SEO ranking factor, an attacker who compromises a large number of sites can game search engine rankings in a big way.
Many of our respondents used the term “pharma hack” to describe this type of attack, because it has recently been used a lot to boost the rankings of pharmaceutical sales sites.
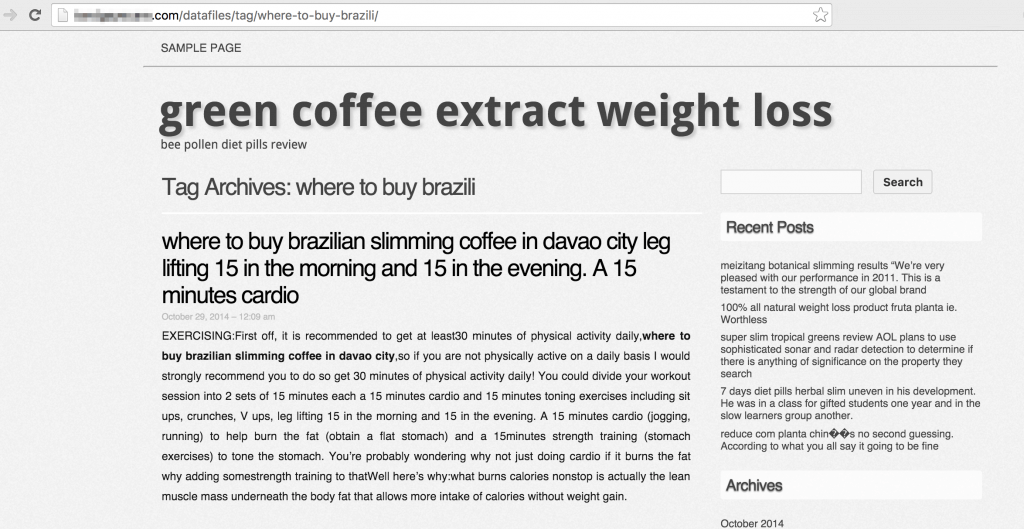
Example of an html page that an attacker hid on an infected site.
What’s in it for the attacker?
As I’m sure most of you know, ranking well for popular search terms is a great way to drive traffic to websites. By gaming the system with SEO spam, attackers are able to divert traffic away from legitimate sites toward their own.
Malicious Redirect
Redirects are an incredibly effective way for attackers to funnel traffic to malicious websites. The unsuspecting user doesn’t have to click on a hyperlink or advertisement for it to work, they are taken there directly.
Sometimes the attacker will take a very aggressive approach, redirecting all traffic to a malicious site or sites. But in many cases the attackers will employ measures to avoid detection, such as only redirecting some URL requests, and in some cases only activating the redirect for specific browsers or device types.
What’s in it for the attacker?
The motive here is simply to drive traffic to their malicious content.
Host Phishing Page
Phishing pages attempt to fool the visitor into providing sensitive information. In some cases they impersonate a bank or retailer and try to get you to give them valuable information like credit card numbers directly. In others they try to capture your username and password to various sites, including your WordPress site if you’re not careful.

Phishing page example courtesy of eff.org
What’s in it for the attacker?
The value of your credit card number is obvious. They can use other data to break into important online accounts, use it for social engineering or spear phishing attacks or to steal your identity.
Distribute Malware
Once they have compromised your site, attackers can install malware that in turn installs malware on your website visitor’s computers without their knowledge. This is an incredibly scary proposition for you as a site owner.
If Google detects that it is happening they will flag your site via their safe browsing program. This will cause your SEO traffic to drop significantly. For more details please read our recent blog post on the impact of a hacked website on SEO. Worse than that, site visitors that are infected will not be happy with you.
The impact to your reputation could be significant and long lasting. Luckily only 2.9% of respondents reported this.
What’s in it for the attacker?
Installing malware on hundreds or thousands of your site visitor’s computers gives the attacker direct access to steal information or wreak havoc on them.
Steal User Data
Given that most people we talk to assume that attackers are interested in stealing their data, we were surprised to learn that only 1.1% of our respondents reported it happening.
We think the main reason is that the majority of WordPress sites do not store sensitive data beyond user credentials for that site and maybe email addresses. It would also be very difficult for the owner of a hacked site to detect data theft if it occurred, so the numbers are likely understated.
What’s in it for the attacker?
Stolen user credentials could be used to regain entry to the site, even if the site has been cleaned. The username / password combinations can also be attempted on other sites in hopes that the user is repeating use of passwords.
Stolen email addresses can be used for spamming. Obviously more sensitive information like credit card numbers would be even more valuable.
Attack Site
In some cases an attacker will decide to use your web server as a platform to launch attacks on other websites. This is relatively rare based on our respondents, who only reported this happening 0.7% of the time.
What’s in it for the attacker?
The attacker gets to use your server free of charge for their malicious activities. They also are much more likely to slip past their targets’ defenses with the attack originating from your domain and IP address. At least until they ruin your reputation.
Ransomware
Ransomware is malicious software that blocks access to your website and demands that you pay a ransom in return for having access restored. This kind of attack has been receiving a lot of attention on blogs and in the press recently. So we were surprised to have only 0.6% of respondents report it.
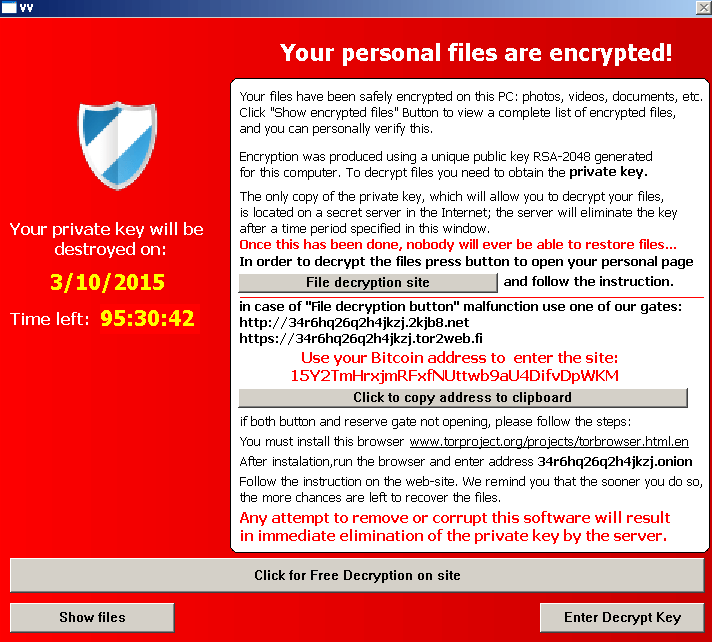
A screenshot of the screen that TeslaCrypt displays when your files are encrypted. Courtesy Bromium Labs.
What’s in it for the attacker?
If you don’t have backups that you were able to keep out of the hands of the attacker, you may decide that paying the ransom is worth it.
Host Malicious Content
Hackers will very often use your web server to host malicious files that they can call from other servers. They are essentially quietly using your hosting account as a file server.
What’s in it for the attacker?
The attacker gets to store their files free of charge on a server with a domain and IP address that have a squeaky clean reputation.
Referrer Spam
If you use Google Analytics you are likely familiar with referrer spam. Referrer spam is bot traffic to your site set up to look like it is coming from a fake referrer. The spammer is trying to get the website owner to check out where the traffic is coming from, driving traffic to the site.
Referrer spam example courtesty of phpmatters.com
What’s in it for the attacker?
As with a lot of the nefarious attacker activities we have already described, they get to use your server free of charge under the cover of your pristine IP address. Their ultimate goal is to drive traffic to one of their websites for reasons that often turn out to be malicious.
This post originally appeared on the Wordfence Blog
Drop your comments below…